Secure your LDAP Server connection between the client and server application to encrypt the communication. Choose Select a server from the server pool option & Select ldap server from the server pool and click on Next button.
1. Install Certificate Authority, Create and Export the certificate
1.1 Install “Active Directory Certificate Services” role through Server Manager roles.
- Log On to Windows Server 2022, click on Start -> Server Manager -> Manage -> Add Roles and Features.

Click on Next

Choose Role-based or feature-based installation option and Click on Next button.

Choose Select a server from the server pool option & Select ldap server from the server pool and click on Next button.

Choose Active Directory Certificate Services option from the list of roles and click on Add Features and then click on Next button.


Leave default settings from the list of features and click on Next button.

In Active Directory Certificate Services (AD CS), Click on Next button.

Select Certification Authority from the list of roles and Click on Next button.

Click on Install button to confirm installation.

Now, click on Configure Active Directory Certificate Services on Destination Server option and click on Close button

We can use the currently logged on user to configure role services since it belongs to the local Administrators group. Click on Next button.

Select Certification Authority from the list of roles and Click on Next button.

Select Enterprise CA option and Click on Next.

Select Root CA option and Click on Next.

Select Create a new private key option and Click on Next button.

- Choose SHA512 as the hash algorithm and Click on Next.
UPDATE : Recommended to select the most recent hashing algorithm.

Click on Next button.

Click on Next button.

Select the default database location and Click on Next.

Click on Configure button to confirm.

Once the configuration succeeded then click on Close button.

1.2 Create a certificate template
Go to Windows Key+R and run certtmpl.msc command and choose the Kerberos Authentication Template.

Right-click on Kerberos Authentication and then select Duplicate Template.

- The Properties of New Template will appear. Configure the setting according to your requirements.
- Go to the General tab and Enable publish certificate in Active Directory option.

Go to the Request Handling Tab and Enable ‘Allow private key to be exported’ option.

Go to the Subject Name tab and Enable subject name format as DNS Name and click on Apply & OK button.

1.3 Issue certificate template
Go to Start -> Certification Authority Right click on “Certificate Templates” and select New-> Certificate Template to Issue.


Now, select your recently created Certificate Template and click on OK button.


1.4 Request new certificate for created certificate template ( ADCS-LDAPS )
Go to Windows Key+R -> mmc -> File -> Add/Remove snap-in. Select Certificates, and click on Add button and then click on Ok button




Now, right Click on Certificates select All Tasks and click on Request for new Certificate.

Click on Next button

Click on Next button

Select ADCS-LDAPS in Active Directory Enrollment Policy and then Click Enroll

Click on Finish


1.5 Test LDAPS Connection using LDP.EXE
Select Start >> All Program >> Windows Support Tools >> Command Prompt. On the command line, type IDP to start the tool.

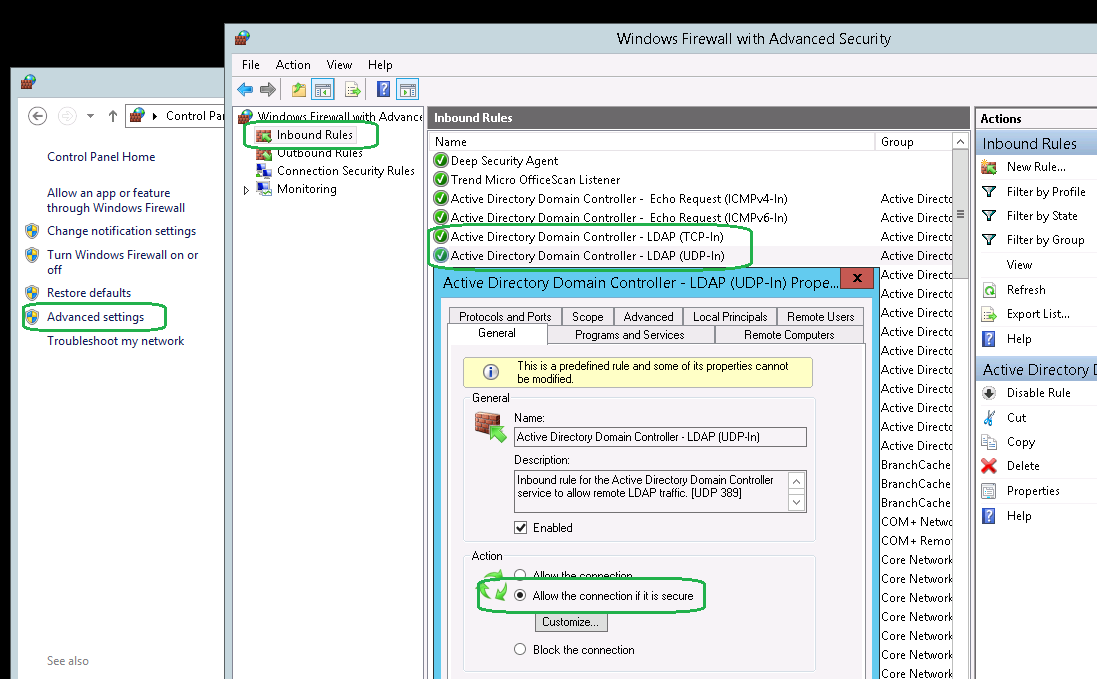
From the IDP window, select Connection >> Connect and type the local FQDN ex: dc01.myousufali.labs and port number (636). Also select the SSL.

Click on OK

2. Configure LDAPS on the client-side server
2.1 Export the created LDAPS certificate
Go to Windows Key+R -> mmc -> File -> Add/Remove snap-in. Select Certificates, and click on Add button and then Select Computer Account Click Next then again Select Local Computer click on Finish button and last OK Button.




Now, right Click on Certificates select All Tasks and click on Export….

Click on Next button

Select No, do not export the private key then Click Next button.

Select Base-64 encoded X .509 file format and click on Next.

Export the .CER to your local system path and click on Next.

Click on Finish button.


Click OK button to finish export.
2.2 Connect your Linux server with Active Directory ( LDAPS )
Convert Certificate Format and Install the Certificate using OpenSSL
- Run the following command to install the Openssl.
- For Ubuntu:
sudo apt-get install openssl
- For RHEL/CentOS:
sudo yum install openssl
- Copy the certificate file you generated in the previous step to the machine on which PHP is running. Run the following command:
For example:/openssl x509 -in LDAPS.cer -out LDAPS.pemThis creates the certificate file in a form that OpenLDAP Client Library can use. - Place the .pem file generated in a directory of your choosing (/etc/openldap/ may be a good choice since that directory already exists.)
- Add the following line to your ldap.conf file:
TLS_CACERT /etc/openldap/LDAPS.pem - This directive tells the OpenLDAP Client Library about the location of the certificate, so that it can be picked up during initial connection.
- For Ubuntu:
2.3 Test Connection
For Linux:
# Without security portldapsearch -H ldap://dc01.myousufali.labs:389 -D 'CN=DC01,OU=IT,OU=Enterprise,DC=myousufali,DC=labs' -w P@ssword9a! -b "dc=myousufali,dc=labs" -s sub "(objectClass=user)" givenName
# With security portldapsearch -ZZ -H ldaps://dc01.myousufali.labs:636 -D 'CN=DC01,OU=IT,OU=Enterprise,DC=myousufali,DC=labs' -w P@ssword9a! -b "dc=myousufali,dc=labs" -s sub "(objectClass=user)" givenName
- ZZ: Start TLS (for LDAPS)
- h: IP/hostname of Active Directory server
- D: BindDN or User principal name
- W: Password (to be provided interactively)
- b: Base DN for search (where in the LDAP tree to start looking)
- s: One of base, one, sub or children (search scope)
For Windows:
- For Windows:
- You can obtain this software from here: http://gnuwin32.sourceforge.net/packages/openssl.htm if you don’t already have it.
- Copy the certificate file you generated in the previous step to the machine on which PHP is running. Run the following command:
For example:C:\openssl\openssl x509 -in LDAPS.cer -out LDAPS.pemThis creates the certificate file in a form that OpenLDAP Client Library can use. - Place the .pem file generated in a directory of your choosing (C:\openldap\sysconf may be a good choice since that directory already exists.)
- Add the following line to your ldap.conf file:
TLS_CACERT C:\openldap\sysconf\LDAPS.pem - This directive tells the OpenLDAP Client Library about the location of the certificate, so that it can be picked up during initial connection.